SigintOS: A Linux Distro for Signal Intelligence
Recently we've heard of a new Linux distribution called SigintOS becoming available for download. SigintOS is an Ubuntu based distribution with a number of built in signal intelligence applications for software defined radios such as RTL-SDRs and other TX capable SDRs like the HackRF, bladeRF and USRP radios.
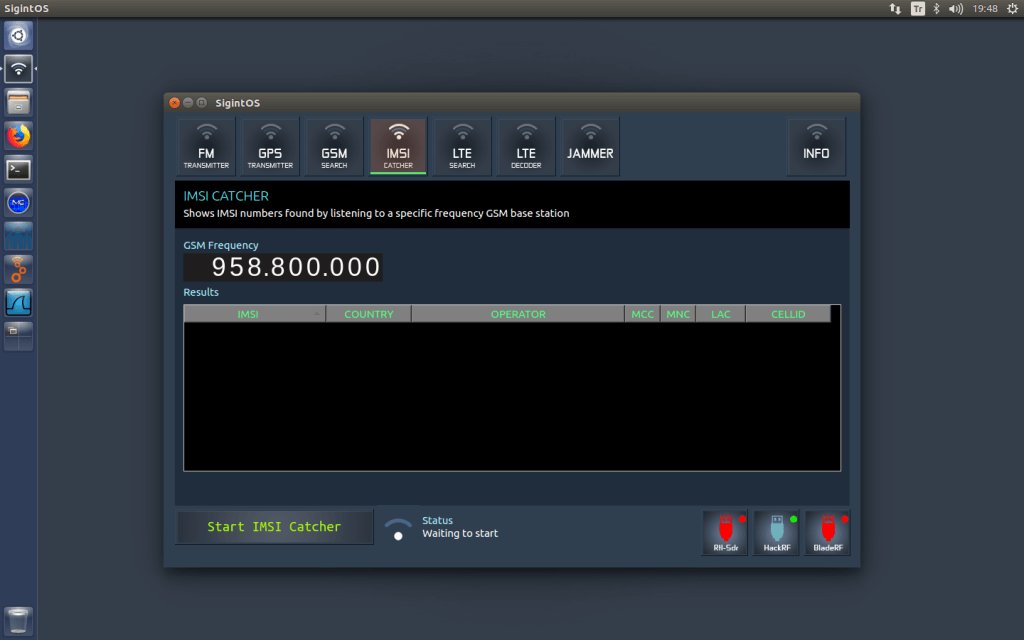
The distro appears to be very well executed, with a built in GUI that grants easy access to the some common sigint tools like an FM and GPS transmitter, a jammer, a GSM base station search tool and an IMSI catcher. SigintOS also has various other preinstalled programs such as GNU Radio, gr-gsm, YatesBTS, wireshark and GQRX.
The OS also teases an LTE search and LTE decoder which to access requires that you get in contact with the creators, presumably for a licencing fee. Regarding an LTE IMSI catcher they write:
LTE IMSI Catcher is not myth!
Due to the nature of LTE base stations, the capture of IMSI numbers seems impossible. LTE stations use GUTI to communicate with users instead of IMSI. The GUTI contains the temporary IMSI number called T-IMSI. This allows the operator to find out who is at the corresponding LTE station who is authorized to query T-IMSI information.
Can the GUTI number be found?
Answer Yes!How to find GUTI and T-IMSI numbers?
Can be found with the help of SigintOS …For detailed information [email protected]
The image comes as a 2GB ISO file, and it's possible to run it in WMWare or VirtualBox.