Bypassing Chamberlain myQ Garage Doors with a Jamming SDR Attack
McAfee Advanced Threat Research have recently uploaded a blog post describing how they investigated Chamberlain’s MyQ Hub, a “Universal” IoT garage door automation platform. Such a device allows you to operate and monitor the status your garage door remotely via an app. This can allow you to open and close the garage door for couriers, or for couriers to do it themselves if they are on the app.
Whilst they found that the internet based network side was secure, they discovered a flaw in the way that the MyQ hub communicates with the remote sensor over RF radio frequencies.
Although the system utilizes rolling codes for security, McAfee researchers made use of the "rolljam" technique, which is one well known method for breaking rolling code security. The basic idea is to use an SDR or other RF device to jam the signal, collect the second rolling code after two key presses, then play back the first. Now the attacker has the second unused rolling code ready to be played back at any time.
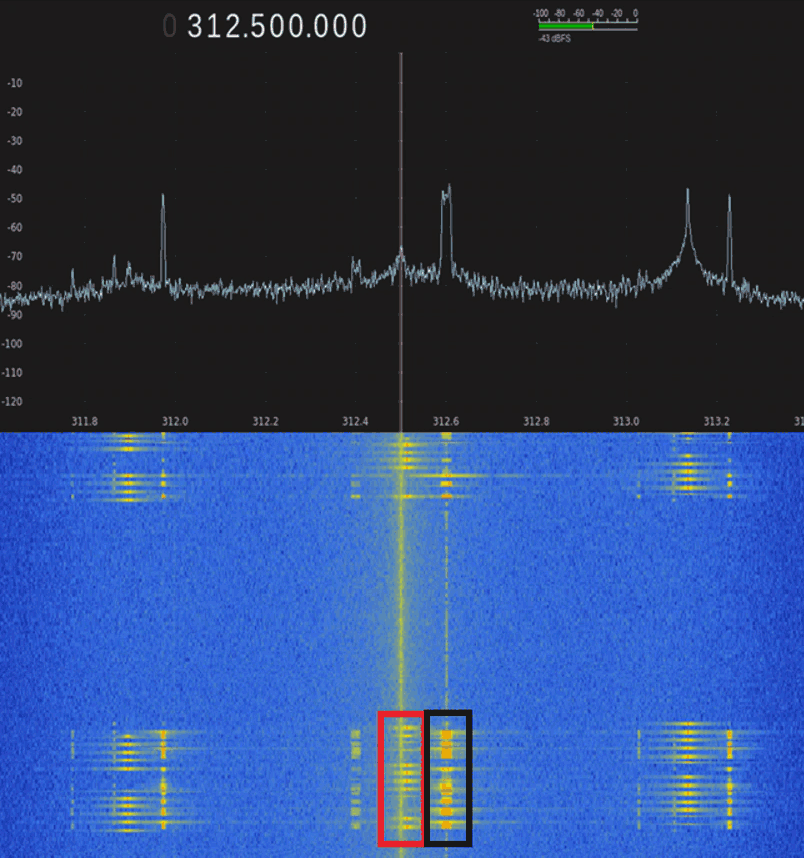
In their threat demonstration they utilized a SDR running GNU Radio on a computing platform which sits outside the target garage door. The method used in the demonstration actually only involves jamming and not the use of a replay. It exploits a method that confuses the state of the MyQ device, allowing the garage door to be mistakenly opened by the owner when he thinks that he is closing it. They write:
With our jamming working reliably, we confirmed that when a user closes the garage door via the MyQ application, the remote sensor never responds with the closed signal because we are jamming it. The app will alert the user that “Something went wrong. Please try again.” This is where a normal user, if not in direct sight of the garage door, would think that their garage door is indeed open, when in reality it is securely closed. If the user believes the MyQ app then they would do as the application indicates and “try again” – this is where the statelessness of garage doors comes into play. The MyQ Hub will send the open/closed signal to the garage door and it will open, because it is already closed, and it is simply changing state. This allows an attacker direct entry into the garage, and, in many cases, into the home.