Michael Ossmann & Kate Temkin Present Software Defined Everything with GreatFET One
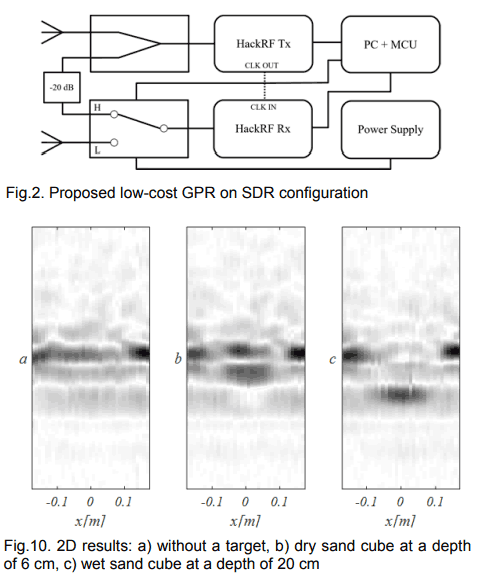
At the Hackaday Supercon Michael Ossmann & Kate Temkin presented a talk called "Software-Defined Everything" where they demonstrated some applications of the "GreatFET One" interface board. Michael Ossmann is best known for creating the HackRF software defined radio which is a highly versatile and low cost open hardware/software SDR transceiver. His company Great Scott Gadgets also employs Kate Temkin who is the lead software developer who worked on their latest product called the GreatFET One.
The GreatFET One is a multi-purpose digital interface board that plugs into a PC via USB. It contains multiple digital IO pins, supports SPI, I2C, UART and JTAG serial protocols, can do logic analysis, and also has a built in ADC and DAC.
In the talk Michael and Kate show how a simple light sensor can be plugged into the GreatFET's ADC, allowing the sensor's data to be digitized and processed in GNU Radio. This results in a software defined light sensor. By analyzing the light data in the frequency domain via an FFT graph they're able to determine the refresh rate of the ceiling lights.
Later they also show how GreatFET can be combined with i2C sensors and GNU Radio to do creative things like use an accelerometer as a microphone for a guitar pickup, with audio effects like guitar clipping controlled by GNU Radio blocks.