Deep-Tempest: Eavesdropping on HDMI via SDR and Deep Learning
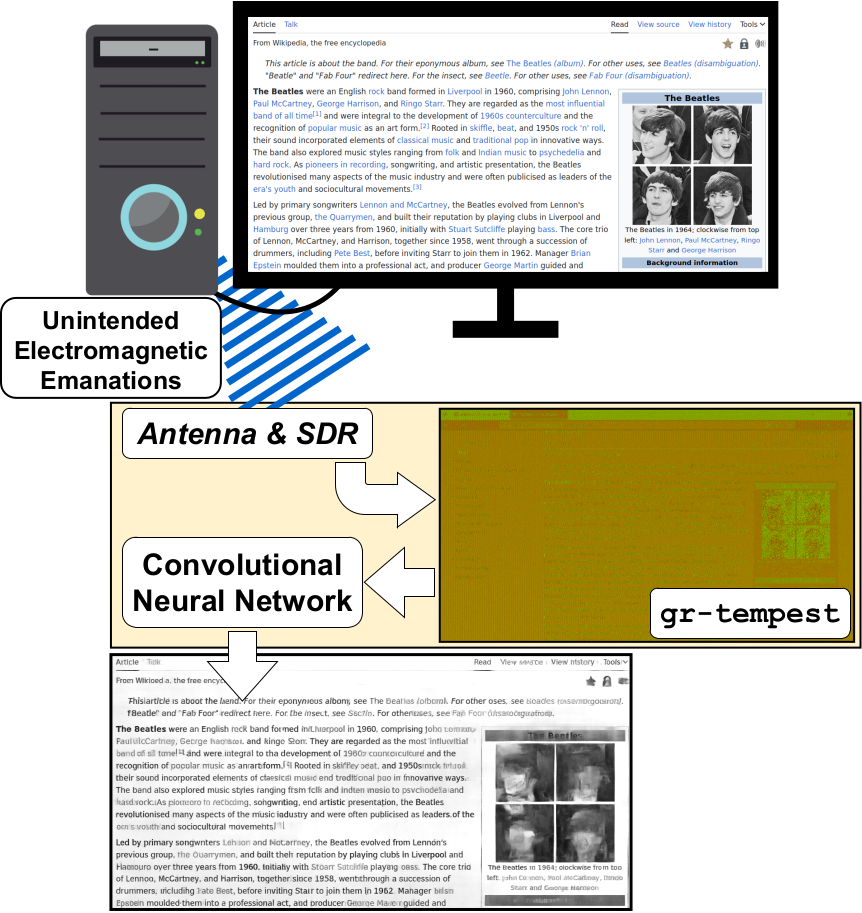
Over the years we've posted several times about the TEMPEST applications of software-defined radio. TEMPEST aka (Van Eck Phreaking) is when you listen to the unintentional RF emissions of electronics and are able to recover information from that. In the past, we posted about TempestSDR, an RTL-SDR compatible program that allows you to view images from a computer monitor or TV simply by picking up the unintentional RF emissions from it.
Usually, the images received are fuzzy and it can be difficult to recover any information from them. However recently there has been work on combining Tempest techniques with deep learning AI for improving image quality.
Deep-tempest has recently been released on GitHub and from their demonstrations, the ability to recover the true image with deep learning is very impressive. From a fuzzy grey screen, they show how they were able to recover clear text which looks almost exactly like the original monitor image.
Deep-tempest is based on gr-tempest, and requires GNU Radio, Python 3.10 and a Conda environment. Instructions for installing it are on the GitHub.
The whitepaper on the University research done to implement Deep-Tempest can be found freely on arxiv at https://arxiv.org/pdf/2407.09717.